Solving a Variety of Office Computer Problems (Case Study)
 Many of my service calls only involve 1 or 2 problems. Today’s service call was different. This afternoon, I helped a customer with at least 9 different issues.
Many of my service calls only involve 1 or 2 problems. Today’s service call was different. This afternoon, I helped a customer with at least 9 different issues.
I arrived after lunch to help a local small business complete their move into a new office. As is sometimes the case, when I finished the main things the business owner (we’ll call him Jeff) had called me out for, he had a few additional things he needed a bit of help with.
Networking Issues: Equipment Choice, Cabling, IP Configuration, Loss of Server Access, & Wireless Security
The first (and main) goal was to get their network back up and running. The AT&T field technician was there to install their internet service. Hmm, that was good. It gave me an opportunity to talk with him about the appropriate equipment.
Since the existing networking equipment Jeff had brought over from the previous office only included a switch, I told the AT&T man we’d need something with some routing capabilities rather than just a modem. He began setting them up with a Netopia 3000-Series Internet Gateway while I had a look at the cables.
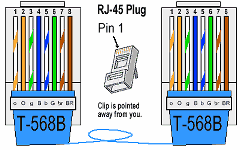
Jeff had already run the appropriate cables from room to room, but they didn’t have any cable ends on them.
In order to do cables, you have to have an appropriate cable-end tool, the new cable connectors, and know the appropriate order to put the wires in (see above for an example). I had time to complete a few cable connectors while the Netopia was being configured.
The AT&T man announced he was finished, so I tried to pull up a web page with the server. No go. “It’s probably still pointing to that device,” the AT&T man suggested. “I wouldn’t think so,” I replied. The existing device was a switch, so it doesn’t do DCHP. Nor, being an unmanaged switch, would it have an IP address to point to.
After a moment’s thought, the issue was pretty obvious: hard-coded IP configuration on the server. I changed it to read from our new Internet Gateway, and we were on our way.
Next was the fact that the Jeff’s desktop suddenly couldn’t connect to their server. Cause: Norton Internet Security on Jeff’s computer wasn’t familiar with the new network.
I finished up connectors for all the computers and the network printer and tested everything. All the cable ends were good, and everything worked.
Finally in the networking category, there was the issue of wireless networking. The device chosen had wireless built in, so the AT&T man had set them up… with WEP for encryption.
“Why don’t you guys set people up with WPA?” I asked the AT&T man. “Since WEP is inherently insecure, why does AT&T have their techs use it?” (I’ve previously blogged on the insecure nature of this setup.)
“Honestly,” he said, “I don’t know.” The company apparently just tells its techs to do it that way, so that’s how he was doing it.
So after I finished up the other networking tasks, I set them up securely. WPA is secure — if you do it right. If you don’t, it’s no better than WEP.
An Outlook Email Annoyance That Was Driving Jeff Crazy
“Can you have a look at my Outlook?” Jeff asked. “It keeps asking for my user name and password for my Yahoo accounts.”
The accounts referred to make use of Yahoo’s paid POP email for small businesses. But the problem was, they just weren’t working very well.
“Is it all the time, or just some of the time?” I asked. Hmm… intermittent.
“How often do you have this problem?”
About once every 5 minutes or so. All day long.
“This may be an issue on Yahoo’s end,” I said to Jeff. “That being the case, we might not be able to do much about it.”
After a quick inspection I found one thing, though, that we could at least try: disabling Norton’s scanning of inbound email. “I’m willing to try anything,” Jeff said. “This is driving me crazy.”
It made no difference.
However… it turned out that Jeff’s Outlook was set to check his email once every 60 seconds. Was this really necessary?
“Yes,” he said. “I have to. I get very time-sensitive emails. I have to respond to those instantly, or we don’t get the business.”
What about the Yahoo accounts? I asked.
Well… it turned out that the Yahoo-based email accounts weren’t so time sensitive. And this gave rise to an idea.
Since Jeff needed to collect his 4 non-Yahoo based email accounts every 60 seconds, but once per hour was fine for the Yahoo accounts, I split his email accounts into 2 groups.
I set the first group to automatically collect every minute. I set the second group to automatically collect every hour.
Theoretically, that ought to reduce the problem from once every 5 minutes to once or twice per work day.
“I can live with that,” Jeff said.
Security on the Server
“You need to do something with the security on your server,” I told Jeff. “It’s not really bad security… it’s more like no security.”
“I think we have something from Webroot,” Jeff said.
“Right,” I replied. “Spysweeper. But although some versions of Spysweeper come with Antivirus, yours doesn’t. And what you have isn’t actually registered, so even the anti-spyware part probably isn’t doing you a great deal of good.”
I showed him that a) no firewall was active on the server, b) he wasn’t getting the security and reliability updates from Microsoft, and c) there was no antivirus.
The first 2 problems were easy — just turn them on. For the third, we settled in the end on a free antivirus program. There are 3 of these that I use, depending on the situation. The one that I used here has a free option even for businesses. It’s the only antivirus I’ve found that does. It probably isn’t as good as the others that I use, but Jeff and his crew hardly ever even touch the server and they haven’t had a lot of virus problems even with no protection, so they’ll probably do okay with it.
Using Two Monitors With One Computer
“We got rid of a computer and have an extra monitor. Can you make it so this desktop uses both of these screens?” Jeff asked.
“I think we should be able to put that together,” I answered.
I inspected the computer and found we would need a PCIE x16 graphics card. Now usually I should have one of these in my van, but it turned out I accidentally must’ve failed to reorder when I used the last one. Fortunately Jeff was able to have a co-worker grab one from a nearby computer parts shop while I finished up some of my other tasks.
This was the one task in the whole visit that didn’t go quite smoothly. Everything else had been pretty straightforward. Even so, it didn’t take terribly long to come up with a solution.
When working with the original video didn’t work, I installed a DVI-to-VGA adapter onto the new graphics card and thus made use of both the DVI and VGA ports that it possessed. Once I did that, everything from there was smooth sailing.
I showed Jeff and his co-worker how to use their new dual-monitor setup. Needless to say, they were pleased with the change.
Business Software Not Working Over the Network
In the final testing of their systems, we discovered that one of their main business programs wasn’t working from the computer with the new dual-monitor display.
The likely reason why was obvious. That particular program relied on the server. And on the server, we had activated the firewall. Until then, it’d been completely without any firewall at all. So prime suspect was the firewall.
A few minutes’ research uncovered a number of programs that had to be ignored (that is, not blocked) by the firewall in order for their software to work properly.
After making the appropriate configuration changes, we tested it. All functional. And to head off any future difficulties, I showed Jeff what would happen if the software provider added future modules.
“You might in future see a pop-up window that looks like this,” I said, showing him an image of a similar window that I’d found over the internet. “You can see that it gives you the name of the program’s publisher. All you have to do is, if the publisher is ‘a la mode,’ simply click the ‘Unblock’ button.
“Oh, that’s easy,” Jeff said. “I can do that.”
“By the way,” he added, “I haven’t had a single email error on my desktop since you fixed Outlook. This is great!”
So once again, mission accomplished. This particular service call was perhaps a bit unusual for its variety of issues encountered and dealt with — at least 9 of them in all. But in an office computing environment, diverse and “odd” issues certainly come along from time to time.
Two things contribute to consistently coming up with good solutions: experience of the technician, and his or her creative problem solving skills.
